I’m having a spot of trouble trying to capture and analyze an ldap issue.
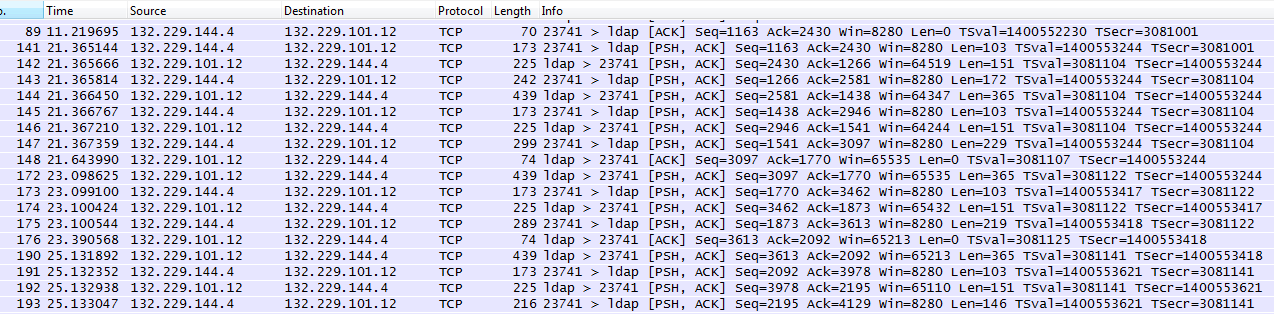
So far we’ve tried to capture the trace at various points in the network (netapp filer, firewall, windows DC), however in all 3 cases wireshark does not dissect the ldap payload, though it recognizes the port correctly as being ldap. Meanwhile traces captured for other clients sending ldap frames to the same DC do dissect perfectly.
I’ve placed below some screenshots (I can’t find a sanitize option, otherwise I would send the trace).
Does anyone have a theory/explanation as to why wireshark is not interpreting the ldap payload in this case? (or even better, a way to trick wireshark into reading this trace as LDAP?)
Thanks,
Mike
Example “good” trace – dissects correctly and displays protocol = “LDAP”

Example “bad” trace – correctly shows the ‘ldap’ port is being used, but does not dissect the load – protocol = “TCP”