Wireshark-dev: Re: [Wireshark-dev] how to decode ULP in TLS
- References:
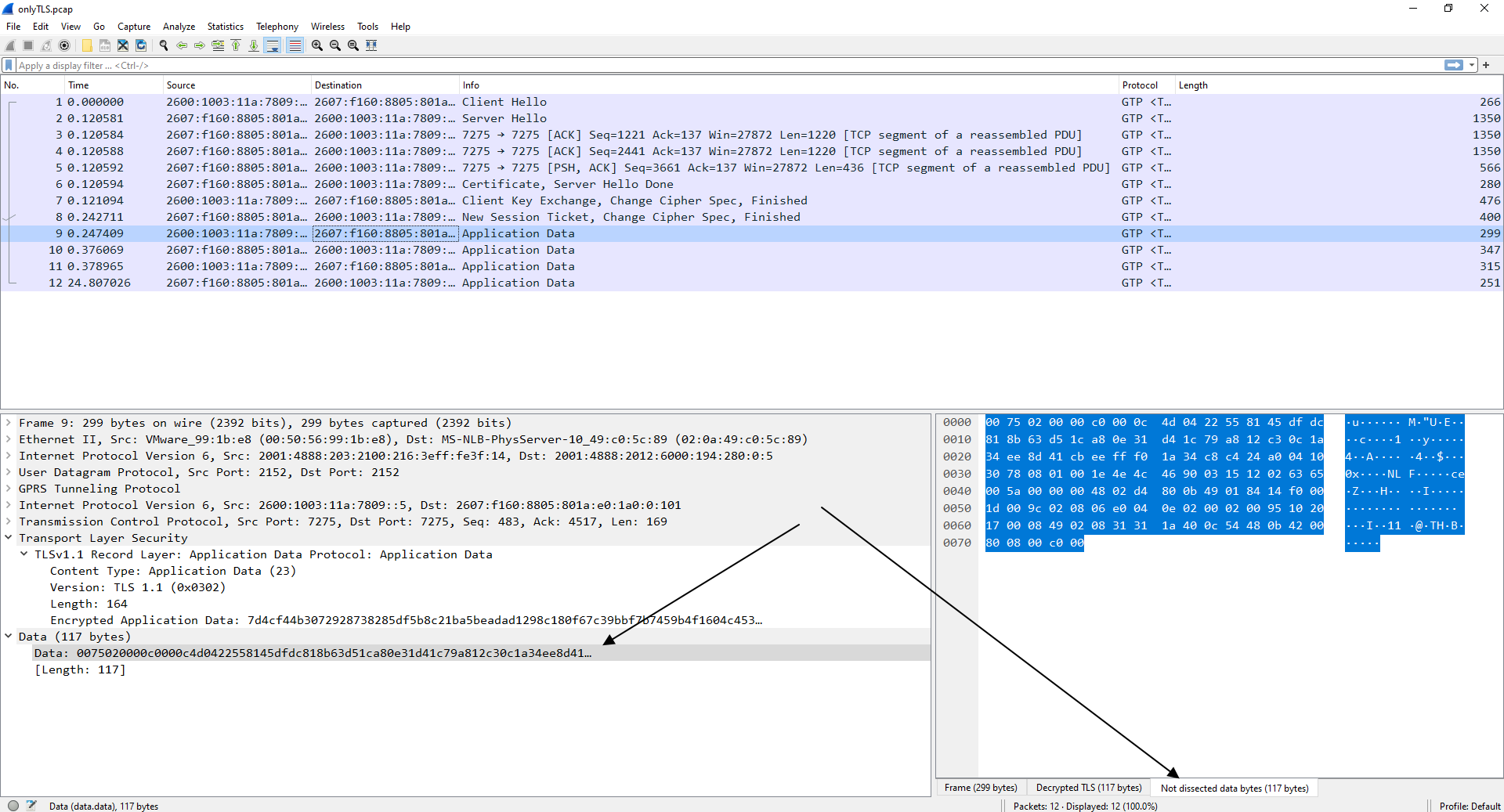
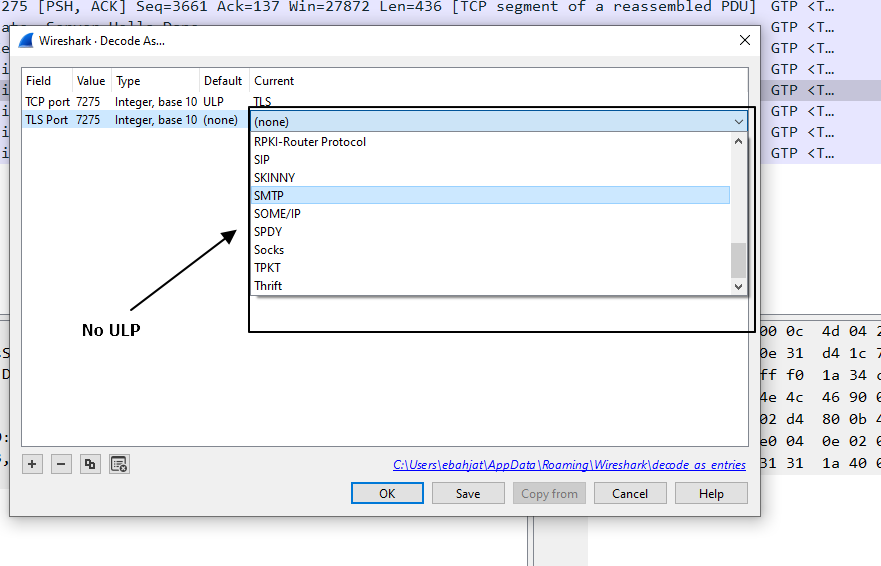
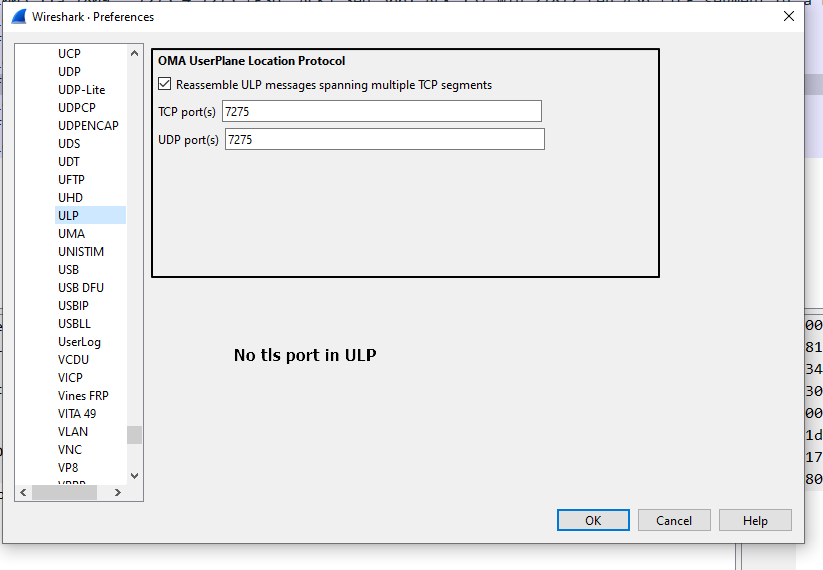
- [Wireshark-dev] how to decode ULP in TLS
- From: Bahjat, Ehab
- [Wireshark-dev] how to decode ULP in TLS
- Prev by Date: Re: [Wireshark-dev] RTP player on Windows/Qt 6.x do not play any sound
- Next by Date: Re: [Wireshark-dev] how to decode ULP in TLS
- Previous by thread: [Wireshark-dev] how to decode ULP in TLS
- Next by thread: Re: [Wireshark-dev] how to decode ULP in TLS
- Index(es):