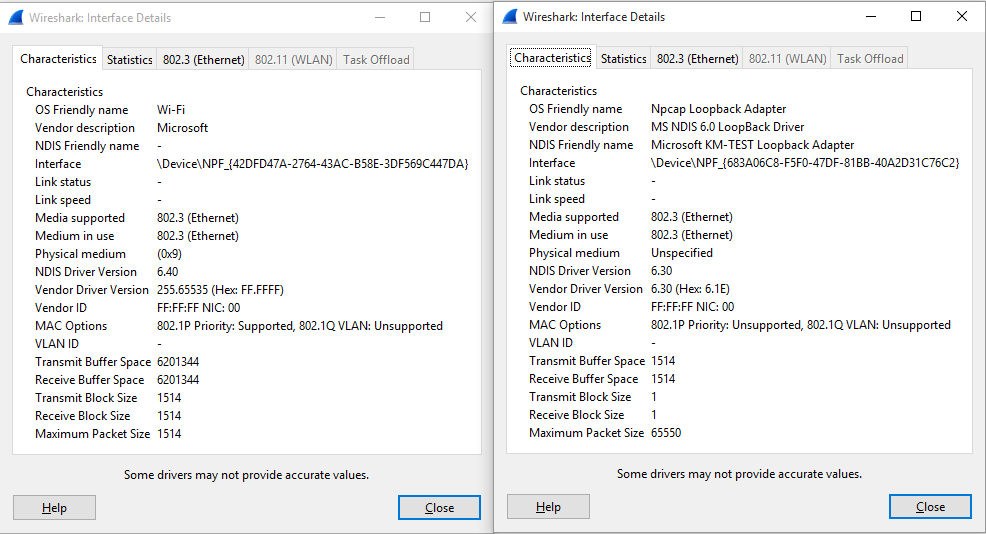
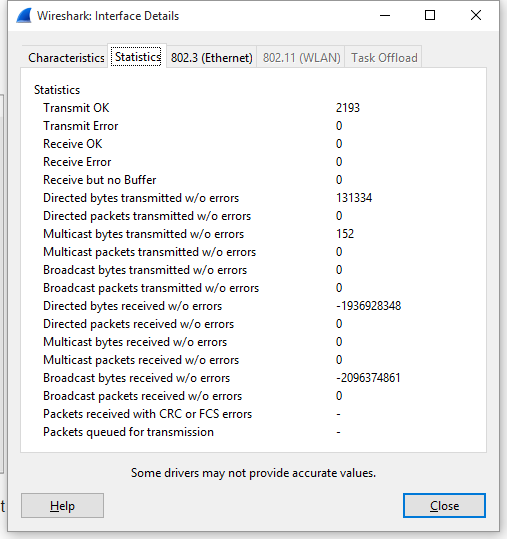
Wireshark-dev: Re: [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65
- References:
- [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65536
- From: Yang Luo
- Re: [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65536
- From: Pascal Quantin
- Re: [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65536
- From: Yang Luo
- Re: [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65536
- From: Pascal Quantin
- [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65536
- Prev by Date: Re: [Wireshark-dev] Bug in Wireshark Display filter engine caused by optimization of proto tree during dissect
- Next by Date: Re: [Wireshark-dev] Bug in Wireshark Display filter engine caused by optimization of proto tree during dissect
- Previous by thread: Re: [Wireshark-dev] Question about changing Npcap loopback interface's MTU to 65536
- Next by thread: [Wireshark-dev] Bug in Wireshark Display filter engine caused by optimization of proto tree during dissect
- Index(es):