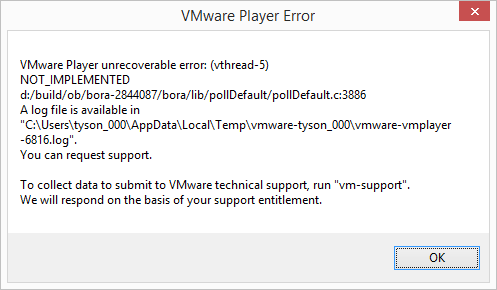
Wireshark-dev: Re: [Wireshark-dev] Npcap 0.03 call for test
From: Tyson Key <tyson.key@xxxxxxxxx>
Date: Sat, 1 Aug 2015 23:12:04 +0100
Oops, it seems that I did all of that testing, against the wrong version (a 0.01 build, instead of 0.03) - but still, some of this info maybe useful :(
--
Tyson.
2015-08-01 22:48 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:
Aah, if I disable using the .NET Reference Source Symbol Service, and restart WinDBG, I can receive the following information:Microsoft (R) Windows Debugger Version 6.3.9600.17336 AMD64Copyright (c) Microsoft Corporation. All rights reserved.Loading Dump File [C:\Windows\MEMORY.DMP]Kernel Bitmap Dump File: Only kernel address space is available************* Symbol Path validation summary **************Response Time (ms) LocationDeferred SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsSymbol search path is: SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsExecutable search path is:Windows 8 Kernel Version 9600 MP (4 procs) Free x64Product: WinNt, suite: TerminalServer SingleUserTS PersonalBuilt by: 9600.17736.amd64fre.winblue_r9.150322-1500Machine Name:Kernel base = 0xfffff800`0ce07000 PsLoadedModuleList = 0xfffff800`0d0e0850Debug session time: Tue Jul 28 16:30:31.391 2015 (UTC + 1:00)System Uptime: 0 days 0:07:03.265Loading Kernel Symbols.........................................................................................................................................................Page 110aba not present in the dump file. Type ".hh dbgerr004" for details..Page 122ed4 not present in the dump file. Type ".hh dbgerr004" for details..................................Loading User SymbolsPEB is paged out (Peb.Ldr = 00007ff7`093db018). Type ".hh dbgerr001" for detailsLoading unloaded module list....................******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************Use !analyze -v to get detailed debugging information.BugCheck C2, {7, 1200, 117ec1, ffffe0015aeeaec8}unable to get nt!MmNonPagedPoolStartunable to get nt!MmSizeOfNonPagedPoolInBytesProbably caused by : NETIO.SYS ( NETIO!NetioCompleteCloneNetBufferListChain+1508d )Followup: MachineOwner---------2: kd> !analyze -v******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************BAD_POOL_CALLER (c2)The current thread is making a bad pool request. Typically this is at a bad IRQL level or double freeing the same allocation, etc.Arguments:Arg1: 0000000000000007, Attempt to free pool which was already freedArg2: 0000000000001200, (reserved)Arg3: 0000000000117ec1, Memory contents of the pool blockArg4: ffffe0015aeeaec8, Address of the block of pool being deallocatedDebugging Details:------------------POOL_ADDRESS: ffffe0015aeeaec8FREED_POOL_TAG: NDndBUGCHECK_STR: 0xc2_7_NDndDEFAULT_BUCKET_ID: WIN8_DRIVER_FAULTPROCESS_NAME: svchost.exeCURRENT_IRQL: 2ANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) amd64freLAST_CONTROL_TRANSFER: from fffff8000d0abff2 to fffff8000cf57ca0STACK_TEXT:ffffd000`9bba4ba8 fffff800`0d0abff2 : 00000000`000000c2 00000000`00000007 00000000`00001200 00000000`00117ec1 : nt!KeBugCheckExffffd000`9bba4bb0 fffff801`14a2f83d : 00000000`00000000 ffffe001`5a593040 000008fe`00000010 00000014`00000011 : nt!ExAllocatePoolWithTag+0x1102ffffd000`9bba4ca0 fffff801`14a013f1 : 00000000`00000000 ffffe001`59b5b600 00000000`00000000 00000000`00000000 : NETIO!NetioCompleteCloneNetBufferListChain+0x1508dffffd000`9bba4d10 fffff801`14d2bc18 : fffff801`14a66228 00000000`00000001 00000000`00000000 00000000`00000000 : NETIO!NetioDereferenceNetBufferListChain+0x2d1ffffd000`9bba4db0 fffff801`14d0118c : ffffe001`5de21fcc 00000000`0000a567 00000000`00000000 00000000`00000000 : tcpip!TcpFlushDelay+0x88ffffd000`9bba4e60 fffff801`14d36f9f : ffffe001`5a527d80 ffffd000`9bba350b ffffd000`9bba81c1 ffffe001`5a4f81c1 : tcpip!TcpPreValidatedReceive+0x3ccffffd000`9bba4f60 fffff801`14d33143 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!IppDeliverListToProtocol+0x4fffffd000`9bba5020 fffff801`14d31525 : 00000000`00000000 00000000`00000000 00000000`00000000 ffffd000`9bba5128 : tcpip!IppProcessDeliverList+0x63ffffd000`9bba50c0 fffff801`14ce9c9d : 00000000`00000000 00000000`00000000 00000000`00000000 ffffd000`9bba52d8 : tcpip!IppReceiveHeaderBatch+0x235ffffd000`9bba51f0 fffff801`14ce91cc : ffffd000`9bba5300 00000000`00000000 ffffe001`5cdfa540 ffffd000`9bba5440 : tcpip!IppLoopbackIndicatePackets+0x39dffffd000`9bba52d0 fffff801`14d06eb8 : ffffe001`59e84600 346dc5d6`38865900 ffffd000`9bba5500 00000000`00000000 : tcpip!IppLoopbackEnqueue+0x3dcffffd000`9bba5400 fffff801`14d06389 : fffff801`14e81180 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!IppDispatchSendPacketHelper+0x398ffffd000`9bba5590 fffff801`14d0491e : ffff0014`00000001 ffffe001`5a4bc568 00000000`00000002 ffffd000`9bba59e0 : tcpip!IppPacketizeDatagrams+0x2d9ffffd000`9bba5730 fffff801`14d09ab7 : fffff801`14cca4f0 00000000`00000007 fffff801`14e81180 ffffe001`5c76f8c0 : tcpip!IppSendDatagramsCommon+0x49effffd000`9bba5910 fffff801`14cff435 : ffffd000`9bba5cf2 00000000`00000000 ffffe001`5caff550 ffffd000`9bba5f90 : tcpip!TcpTcbSend+0x55bffffd000`9bba5c60 fffff801`14cff07c : 00000000`0000a567 ffffe001`5c76f8c0 ffffd000`9bba5cf1 ffffd000`9bba5f00 : tcpip!TcpEnqueueTcbSendOlmNotifySendComplete+0xa5ffffd000`9bba5c90 fffff801`14cff538 : ffffc001`5b0b1b02 00000000`00000000 ffffe001`5dbf5100 00000000`0ce5a000 : tcpip!TcpEnqueueTcbSend+0x2acffffd000`9bba5d90 fffff800`0ce79703 : ffffe001`5dbf51e0 fffff801`14cff7f6 fffff801`14cff510 ffffd000`9bba5e50 : tcpip!TcpTlConnectionSendCalloutRoutine+0x28ffffd000`9bba5e10 fffff801`14cff7f6 : fffff801`14cff510 ffffd000`9bba5f30 ffffc001`5b0b1e00 00000000`00000000 : nt!KeExpandKernelStackAndCalloutInternal+0xf3ffffd000`9bba5f00 fffff801`15402ecf : ffffe001`5dbf51e0 ffffe001`59f3c4c0 00000000`00000000 ffffe001`5db660c0 : tcpip!TcpTlConnectionSend+0x76ffffd000`9bba5f70 fffff801`184e7860 : ffffe001`5c7b9cb0 00000000`00000002 ffffe001`5db660c0 ffffe001`5c75b050 : afd!WskProIRPSend+0xbfffffd000`9bba5fe0 fffff801`184e647c : 00000000`ffffffff ffffe001`59fc96f8 00000580`00000000 fffffa80`001ca790 : HTTP!UxTlInitiateSend+0x1e0ffffd000`9bba60a0 fffff801`1855b0ea : ffffe001`59fc96f8 00000000`00000000 00000000`00000001 00000000`00000000 : HTTP!UxpTpFastTransmit+0x19cffffd000`9bba6140 fffff801`184e7cad : ffffe001`59fc9420 fffff801`184e64ff 00000000`00000000 ffffe001`58ef53b0 : HTTP!UxTpTransmitPacket+0xbaffffd000`9bba61e0 fffff801`18559bbf : 00000000`00000000 00000000`00000000 fffff801`18536ae0 ffffe001`58ef53b0 : HTTP!UlSendData+0xddffffd000`9bba6270 fffff801`18574a7f : 00000000`00000000 fffff801`18536ae0 ffffe001`5a211850 ffffe001`5a211850 : HTTP!UlFastSendHttpResponse+0x1765ffffd000`9bba6500 fffff801`184e42b8 : 00000000`00124043 fffff801`1854c180 00000000`00000020 ffffe001`5a2119f8 : HTTP!UlSendEntityBodyIoctl+0xd2fffffd000`9bba6840 fffff800`0d22c77f : 00000000`00000000 ffffd000`9bba6b80 ffffe001`5a211850 00000000`00000004 : HTTP!UlDeviceControl+0x78ffffd000`9bba6880 fffff800`0d22bd22 : ffffd000`9bba6a38 00000000`00000000 00000000`00000000 00000000`00000000 : nt!IopXxxControlFile+0xa4fffffd000`9bba6a20 fffff800`0cf634b3 : ffffe001`58edf080 00000000`001f0003 00000031`01acf0f8 00000000`00000001 : nt!NtDeviceIoControlFile+0x56ffffd000`9bba6a90 00007ff8`24c3123a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x1300000031`01ace928 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`24c3123aSTACK_COMMAND: kbFOLLOWUP_IP:NETIO!NetioCompleteCloneNetBufferListChain+1508dfffff801`14a2f83d 90 nopSYMBOL_STACK_INDEX: 2SYMBOL_NAME: NETIO!NetioCompleteCloneNetBufferListChain+1508dFOLLOWUP_NAME: MachineOwnerMODULE_NAME: NETIOIMAGE_NAME: NETIO.SYSDEBUG_FLR_IMAGE_TIMESTAMP: 540ebbe6BUCKET_ID_FUNC_OFFSET: 1508dFAILURE_BUCKET_ID: 0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChainBUCKET_ID: 0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChainANALYSIS_SOURCE: KMFAILURE_ID_HASH_STRING: km:0xc2_7_ndnd_netio!netiocompleteclonenetbufferlistchainFAILURE_ID_HASH: {ec09700b-3916-f849-b5d5-75c2ba7b02db}Followup: MachineOwner---------This seems a lot more useful, I think...Tyson.2015-08-01 22:43 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Hi Yang,This is something of an anti-climax, after doing the post-mortem (I waited a long time to receive this BSoD! :(), but the means of triggering it are really interesting; and I managed to crash Wireshark itself, before I was able to restart it, and do another trace...I was trying to use Linn Kinsky to play some music via UPnP, on a Raspberry Pi running upmpdcli; and noticed that Asset UPnP (my media streaming server) wasn't being detected as a source in Kinsky, despite the upmpdcli being detected as a "Room"/sink for media playback (due to some problems with multicast traffic, and local unicast server traffic being incorrectly passed into the NPCap Loopback Adapter, instead of my WLAN adapter).So whilst Wireshark was still happily capturing packets (as it had been, for about an hour), I decided to use "Play To" in Windows Media Player, to send/stream an AAC file - which worked, although oddly, I couldn't see all of the traffic between WMP, and upmpdcli, despite capturing on all interfaces at once, after doing diagnostic on my WLAN, a few times; so I started saving the trace, and tried to start a new one. At this stage, Wireshark crashed; and I ended up restarting it, whilst the media was still streaming (and I could now see the HTTP traffic between the two UPnP implementations) - but about 20 minutes later, I received a long-awaited BSoD...WinDBG only seems to give me the following information, which suggests that I may have a problem with some symbol files:Microsoft (R) Windows Debugger Version 6.3.9600.17336 AMD64Copyright (c) Microsoft Corporation. All rights reserved.Loading Dump File [C:\Windows\MEMORY.DMP]Kernel Bitmap Dump File: Only kernel address space is available************* Symbol Path validation summary **************Response Time (ms) LocationDeferred SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbols*http://referencesource.microsoft.com/symbolsSymbol search path is: SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbols*http://referencesource.microsoft.com/symbolsExecutable search path is:*** ERROR: Symbol file could not be found. Defaulted to export symbols for ntkrnlmp.exe -Windows 8 Kernel Version 9600 MP (4 procs) Free x64Product: WinNt, suite: TerminalServer SingleUserTS PersonalBuilt by: 9600.17736.amd64fre.winblue_r9.150322-1500Machine Name:Kernel base = 0xfffff800`0ce07000 PsLoadedModuleList = 0xfffff800`0d0e0850Debug session time: Tue Jul 28 16:30:31.391 2015 (UTC + 1:00)System Uptime: 0 days 0:07:03.265*** ERROR: Symbol file could not be found. Defaulted to export symbols for ntkrnlmp.exe -Loading Kernel Symbols...............Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.Run !sym noisy before .reload to track down problems loading symbols...........................................................................................................................................Page 110aba not present in the dump file. Type ".hh dbgerr004" for details..Page 122ed4 not present in the dump file. Type ".hh dbgerr004" for details..................................Loading User SymbolsPEB is paged out (Peb.Ldr = 00007ff7`093db018). Type ".hh dbgerr001" for detailsLoading unloaded module list....................************* Symbol Loading Error Summary **************Module name Errorntkrnlmp The system cannot find the file specifiedYou can troubleshoot most symbol related issues by turning on symbol loading diagnostics (!sym noisy) and repeating the command that caused symbols to be loaded.You should also verify that your symbol search path (.sympath) is correct.******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************Use !analyze -v to get detailed debugging information.BugCheck C2, {7, 1200, 117ec1, ffffe0015aeeaec8}*** ERROR: Symbol file could not be found. Defaulted to export symbols for NETIO.SYS -*** ERROR: Module load completed but symbols could not be loaded for tcpip.sys*** ERROR: Module load completed but symbols could not be loaded for afd.sys*** ERROR: Module load completed but symbols could not be loaded for HTTP.sys***** Kernel symbols are WRONG. Please fix symbols to do analysis.**************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!PVOID ****** ****************************************************************************unable to get nt!MmSpecialPoolStartunable to get nt!MmSpecialPoolEnd**************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!_POOL_HEADER ****** ****************************************************************************unable to get nt!MmPagedPoolEndunable to get nt!MmNonPagedPoolStartunable to get nt!MmSizeOfNonPagedPoolInBytes**************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!_POOL_HEADER ****** ******************************************************************************************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!_POOL_TRACKER_BIG_PAGES ****** ****************************************************************************Cannot get _POOL_TRACKER_BIG_PAGES type size**************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!_KPRCB ****** ******************************************************************************************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!_KPRCB ****** ******************************************************************************************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!_KPRCB ****** ****************************************************************************Probably caused by : NETIO.SYS ( NETIO!KfdQueryLayerStats+2049 )Followup: MachineOwner---------I'm going to retry analysis with "unqualified symbols" enabled - but I thought that I already had all of these symbols installed (for both System32, and SysWoW64), although maybe they became corrupted during installation?As for the VMware Player issues, I noticed this, in the Event Log:The application (VMware Player, from vendor VMware, Inc.) has the following problem: To function properly, VMware Player must be reinstalled after you upgrade Windows.Since I don't have VMware's proprietary symbols, I only get this information from its coredump - but it may still be interesting...Microsoft (R) Windows Debugger Version 6.3.9600.17336 AMD64Copyright (c) Microsoft Corporation. All rights reserved.Loading Dump File [C:\Users\tyson_000\AppData\Local\Temp\vmware-tyson_000\vmplayer-10248.dmp]User Mini Dump File: Only registers, stack and portions of memory are available************* Symbol Path validation summary **************Response Time (ms) LocationDeferred SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbols*http://referencesource.microsoft.com/symbolsSymbol search path is: SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbols*http://referencesource.microsoft.com/symbolsExecutable search path is:Windows 8 Version 9600 MP (4 procs) Free x86 compatibleProduct: WinNt, suite: SingleUserTS PersonalBuilt by: 6.3.9600.17031 (winblue_gdr.140221-1952)Machine Name:Debug session time: Sat Aug 1 21:51:12.000 2015 (UTC + 1:00)System Uptime: not availableProcess Uptime: 0 days 0:00:22.000.................................................................................................................................This dump file has an exception of interest stored in it.The stored exception information can be accessed via .ecxr.(2808.2818): Unknown exception - code cafebabe (first/second chance not available)*** WARNING: Unable to verify timestamp for ntdll.dll*** ERROR: Module load completed but symbols could not be loaded for ntdll.dlleax=00000000 ebx=05262c20 ecx=00000000 edx=00000000 esi=05262bd8 edi=05262be8eip=76fad28c esp=0734a34c ebp=0734a358 iopl=0 nv up ei pl nz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202ntdll+0x3d28c:76fad28c c20800 ret 80:014> .excr^ Syntax error in '.excr'0:014> !verifyNo export verify found0:014> !validateNo export validate found0:014> !analyze -v******************************************************************************** ** Exception Analysis ** *********************************************************************************** WARNING: Unable to verify timestamp for kernel32.dll*** ERROR: Module load completed but symbols could not be loaded for kernel32.dll***** OS symbols are WRONG. Please fix symbols to do analysis.Unable to load image C:\Windows\System32\KERNELBASE.dll, Win32 error 0n2*** WARNING: Unable to verify timestamp for KERNELBASE.dll*** ERROR: Module load completed but symbols could not be loaded for KERNELBASE.dll**************************************************************************** ****** ****** Either you specified an unqualified symbol, or your debugger ****** doesn't have full symbol information. Unqualified symbol ****** resolution is turned off by default. Please either specify a ****** fully qualified symbol module!symbolname, or enable resolution ****** of unqualified symbols by typing ".symopt- 100". Note that ****** enabling unqualified symbol resolution with network symbol ****** server shares in the symbol path may cause the debugger to ****** appear to hang for long periods of time when an incorrect ****** symbol name is typed or the network symbol server is down. ****** ****** For some commands to work properly, your symbol path ****** must point to .pdb files that have full type information. ****** ****** Certain .pdb files (such as the public OS symbols) do not ****** contain the required information. Contact the group that ****** provided you with these symbols if you need this command to ****** work. ****** ****** Type referenced: nt!IMAGE_NT_HEADERS32 ****** ****************************************************************************Unable to load image C:\Windows\System32\user32.dll, Win32 error 0n2*** WARNING: Unable to verify timestamp for user32.dll*** ERROR: Module load completed but symbols could not be loaded for user32.dll*** ERROR: Symbol file could not be found. Defaulted to export symbols for vmplayer.exe -Unable to load image C:\Windows\System32\ole32.dll, Win32 error 0n2*** WARNING: Unable to verify timestamp for ole32.dll*** ERROR: Module load completed but symbols could not be loaded for ole32.dll************* Symbol Loading Error Summary **************Module name Errorole32 PDB not found : srv*c:\symbols\*http://msdl.microsoft.com/download/symbols*http://referencesource.microsoft.com/symbolsYou can troubleshoot most symbol related issues by turning on symbol loading diagnostics (!sym noisy) and repeating the command that caused symbols to be loaded.You should also verify that your symbol search path (.sympath) is correct.Unable to load image C:\Windows\System32\combase.dll, Win32 error 0n2*** WARNING: Unable to verify timestamp for combase.dll*** ERROR: Module load completed but symbols could not be loaded for combase.dll************* Symbol Loading Error Summary **************Module name Errorcombase PDB not found : srv*c:\symbols\*http://msdl.microsoft.com/download/symbols*http://referencesource.microsoft.com/symbolsYou can troubleshoot most symbol related issues by turning on symbol loading diagnostics (!sym noisy) and repeating the command that caused symbols to be loaded.You should also verify that your symbol search path (.sympath) is correct.*** ERROR: Symbol file could not be found. Defaulted to export symbols for GdiPlus.dll -*** ERROR: Symbol file could not be found. Defaulted to export symbols for nuragoLSPService.DLL -*** WARNING: Unable to verify timestamp for ws2_32.dll*** ERROR: Module load completed but symbols could not be loaded for ws2_32.dll*** WARNING: Unable to verify timestamp for mswsock.dll*** ERROR: Module load completed but symbols could not be loaded for mswsock.dllFAULTING_IP:KERNELBASE+1459876a14598 8b4c2454 mov ecx,dword ptr [esp+54h]EXCEPTION_RECORD: ffffffff -- (.exr 0xffffffffffffffff)ExceptionAddress: 76a14598 (KERNELBASE+0x00014598)ExceptionCode: cafebabeExceptionFlags: 00000000NumberParameters: 0CONTEXT: 00000000 -- (.cxr 0x0;r)eax=00000000 ebx=05262c20 ecx=00000000 edx=00000000 esi=05262bd8 edi=05262be8eip=76fad28c esp=0734a34c ebp=0734a358 iopl=0 nv up ei pl nz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202ntdll+0x3d28c:76fad28c c20800 ret 8DEFAULT_BUCKET_ID: WRONG_SYMBOLSPROCESS_NAME: vmplayer.exeADDITIONAL_DEBUG_TEXT:You can run '.symfix; .reload' to try to fix the symbol path and load symbols.FAULTING_MODULE: 76f70000 ntdllDEBUG_FLR_IMAGE_TIMESTAMP: 558b015cERROR_CODE: (NTSTATUS) 0xcafebabe - <Unable to get error code text>EXCEPTION_CODE: (NTSTATUS) 0xcafebabe - <Unable to get error code text>APP: vmplayer.exeANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) amd64freLAST_CONTROL_TRANSFER: from 6e2ed56a to 6e2ca092PRIMARY_PROBLEM_CLASS: WRONG_SYMBOLSBUGCHECK_STR: APPLICATION_FAULT_WRONG_SYMBOLSSTACK_TEXT:WARNING: Stack unwind information not available. Following frames may be wrong.0734b0d0 6e2ed56a 0734f83b 04693798 5f544f4e vmwarebase!Ordinal478+0xc120734b4e0 6e2ed5b0 6e58c6fc 0734b4fc 0734f84c vmwarebase!Ordinal1473+0xea0734b4f0 6e373e96 6e58c6fc 6e5d1aa4 00000f2e vmwarebase!Ordinal3+0x100734f84c 76807c04 04693798 76807be0 614f3b9d vmwarebase!Ordinal1438+0x2fa60734f860 76fcad1f 04693798 60d8b8da 00000000 kernel32+0x17c040734f8a8 76fcacea ffffffff 76fb021c 00000000 ntdll+0x5ad1f0734f8b8 00000000 6e373bf0 04693798 00000000 ntdll+0x5aceaFOLLOWUP_IP:vmwarebase!Ordinal478+c126e2ca092 8f8570fdffff pop dword ptr [ebp-290h]SYMBOL_STACK_INDEX: 0SYMBOL_NAME: vmwarebase!Ordinal478+c12FOLLOWUP_NAME: MachineOwnerMODULE_NAME: vmwarebaseIMAGE_NAME: vmwarebase.DLLSTACK_COMMAND: ~14s; .ecxr ; kbBUCKET_ID: WRONG_SYMBOLSFAILURE_BUCKET_ID: WRONG_SYMBOLS_cafebabe_vmwarebase.DLL!Ordinal478ANALYSIS_SOURCE: UMFAILURE_ID_HASH_STRING: um:wrong_symbols_cafebabe_vmwarebase.dll!ordinal478FAILURE_ID_HASH: {e43078e2-dbb2-d9e8-8a03-1b6323ba8806}Followup: MachineOwner---------0:014> .symfix; .reload.................................................................................................................................0:014> !analyze -v******************************************************************************** ** Exception Analysis ** *********************************************************************************** ERROR: Symbol file could not be found. Defaulted to export symbols for vmplayer.exe -*** ERROR: Symbol file could not be found. Defaulted to export symbols for nuragoLSPService.DLL -FAULTING_IP:KERNELBASE!RaiseException+4876a14598 8b4c2454 mov ecx,dword ptr [esp+54h]EXCEPTION_RECORD: ffffffff -- (.exr 0xffffffffffffffff)ExceptionAddress: 76a14598 (KERNELBASE!RaiseException+0x00000048)ExceptionCode: cafebabeExceptionFlags: 00000000NumberParameters: 0CONTEXT: 00000000 -- (.cxr 0x0;r)eax=00000000 ebx=05262c20 ecx=00000000 edx=00000000 esi=05262bd8 edi=05262be8eip=76fad28c esp=0734a34c ebp=0734a358 iopl=0 nv up ei pl nz na po nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000202ntdll!NtGetContextThread+0xc:76fad28c c20800 ret 8DEFAULT_BUCKET_ID: APPLICATION_FAULTPROCESS_NAME: vmplayer.exeERROR_CODE: (NTSTATUS) 0xcafebabe - <Unable to get error code text>EXCEPTION_CODE: (NTSTATUS) 0xcafebabe - <Unable to get error code text>APPLICATION_VERIFIER_FLAGS: 0APP: vmplayer.exeANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) amd64freFAULTING_THREAD: 00002818PRIMARY_PROBLEM_CLASS: APPLICATION_FAULTBUGCHECK_STR: APPLICATION_FAULT_APPLICATION_FAULTLAST_CONTROL_TRANSFER: from 6e2ed56a to 6e2ca092STACK_TEXT:WARNING: Stack unwind information not available. Following frames may be wrong.0734b0d0 6e2ed56a 0734f83b 04693798 5f544f4e vmwarebase!Ordinal478+0xc120734b4e0 6e2ed5b0 6e58c6fc 0734b4fc 0734f84c vmwarebase!Ordinal1473+0xea0734b4f0 6e373e96 6e58c6fc 6e5d1aa4 00000f2e vmwarebase!Ordinal3+0x100734f84c 76807c04 04693798 76807be0 614f3b9d vmwarebase!Ordinal1438+0x2fa60734f860 76fcad1f 04693798 60d8b8da 00000000 kernel32!BaseThreadInitThunk+0x240734f8a8 76fcacea ffffffff 76fb021c 00000000 ntdll!__RtlUserThreadStart+0x2f0734f8b8 00000000 6e373bf0 04693798 00000000 ntdll!_RtlUserThreadStart+0x1bFOLLOWUP_IP:vmwarebase!Ordinal478+c126e2ca092 8f8570fdffff pop dword ptr [ebp-290h]SYMBOL_STACK_INDEX: 0SYMBOL_NAME: vmwarebase!Ordinal478+c12FOLLOWUP_NAME: MachineOwnerMODULE_NAME: vmwarebaseIMAGE_NAME: vmwarebase.DLLDEBUG_FLR_IMAGE_TIMESTAMP: 558b015cSTACK_COMMAND: ~14s; .ecxr ; kbFAILURE_BUCKET_ID: APPLICATION_FAULT_cafebabe_vmwarebase.DLL!Ordinal478BUCKET_ID: APPLICATION_FAULT_APPLICATION_FAULT_vmwarebase!Ordinal478+c12ANALYSIS_SOURCE: UMFAILURE_ID_HASH_STRING: um:application_fault_cafebabe_vmwarebase.dll!ordinal478FAILURE_ID_HASH: {9a30121c-2058-3ec3-2830-959a8e02a5af}Followup: MachineOwner---------I hope that helps,Tyson.2015-08-01 21:20 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:As for the loss of connectivity, Event Viewer just says:Details about network adapter diagnosis:Network adapter Wi-Fi driver information:Description . . . . . . . . . . : Qualcomm Atheros AR9485WB-EG Wireless Network AdapterManufacturer . . . . . . . . . : Qualcomm Atheros Communications Inc.Provider . . . . . . . . . . . : Qualcomm Atheros Communications Inc.Version . . . . . . . . . . . : 10.0.0.242Inf File Name . . . . . . . . . : C:\WINDOWS\INF\oem14.infInf File Date . . . . . . . . . : Friday, March 29, 2013 3:07:20 AMSection Name . . . . . . . . . : ATHR_DEV_OS61_321817AA.ndiHardware ID . . . . . . . . . . : pci\ven_168c&dev_0032&subsys_321817aaInstance Status Flags . . . . . : 0x180200aDevice Manager Status Code . . : 0IfType . . . . . . . . . . . . : 71Physical Media Type . . . . . . : 9Details about wireless connectivity diagnosis:Information for connection being diagnosedInterface GUID: 125860e2-8019-475a-806c-2d553e9e8c8cInterface name: Qualcomm Atheros AR9485WB-EG Wireless Network AdapterInterface type: Native WiFiConnection incident diagnosedAuto Configuration ID: 1Connection ID: 1Connection status summaryConnection started at: 2015-08-01 20:44:24-417Profile match: SuccessPre-Association: SuccessAssociation: SuccessSecurity and Authentication: SuccessList of visible access point(s): 6 item(s) total, 6 item(s) displayedBSSID BSS Type PHY Signal(dB) Chnl/freq SSID-------------------------------------------------------------------------54-A5-1B-FA-0C-B0 Infra <unknown> -91 1 TALKTALK-FA0CA858-98-35-C1-56-4B Infra <unknown> -93 1 JohnLewisWirelessC1564BC4-3D-C7-BF-6F-8E Infra g -70 6 DarkStar80-3F-5D-97-02-08 Infra g -31 6 DarkStarFC-75-16-AE-C3-A4 Infra <unknown> -91 11 TALKTALK-AEC3A460-E7-01-A6-12-F8 Infra <unknown> -91 2 TALKTALKA612F2Connection HistoryInformation for Auto Configuration ID 1List of visible networks: 5 item(s) total, 5 item(s) displayedBSS Type PHY Security Signal(RSSI) Compatible SSID------------------------------------------------------------------------------Infra <unknown> Yes 12 Yes TALKTALK-FA0CA8Infra <unknown> Yes 8 Yes JohnLewisWirelessC1564BInfra g No 100 Yes DarkStarInfra <unknown> Yes 12 Yes TALKTALK-AEC3A4Infra <unknown> Yes 12 Yes TALKTALKA612F2List of preferred networks: 4 item(s)Profile: Canon_ij_SetupSSID: Canon_ij_SetupSSID length: 14Connection mode: InfraSecurity: NoSet by group policy: NoConnect even if network is not broadcasting: NoConnectable: NoReason: 0x00028001Profile: uobroamnetSSID: uobroamnetSSID length: 10Connection mode: InfraSecurity: NoSet by group policy: NoConnect even if network is not broadcasting: NoConnectable: NoReason: 0x00028001Profile: NETGEARSSID: NETGEARSSID length: 7Connection mode: InfraSecurity: NoSet by group policy: NoConnect even if network is not broadcasting: NoConnectable: NoReason: 0x00028001Profile: DarkStarSSID: DarkStarSSID length: 8Connection mode: InfraSecurity: NoSet by group policy: NoConnect even if network is not broadcasting: NoConnectable: YesInformation for Connection ID 1Connection started at: 2015-08-01 20:44:24-417Auto Configuration ID: 1Profile: DarkStarSSID: DarkStarSSID length: 8Connection mode: InfraSecurity: NoPre-Association and AssociationConnectivity settings provided by hardware manufacturer (IHV): NoSecurity settings provided by hardware manufacturer (IHV): NoProfile matches network requirements: SuccessPre-association status: SuccessAssociation status: SuccessLast AP: 80-3f-5d-97-02-08Security and AuthenticationConfigured security type: OpenConfigured encryption type: None802.1X protocol: NoKey exchange initiated: YesUnicast key received: NoMulticast key received: NoNumber of security packets received: 0Number of security packets sent: 0Security attempt status: SuccessConnectivityPacket statisticsNdis Rx: 761Ndis Tx: 1050Unicast decrypt success: 0Multicast decrypt success: 0Unicast decrypt failure: 0Multicast decrypt failure: 0Rx success: 860Rx failure: 36Tx success: 1442Tx failure: 0Tx retry: 199Tx multiple retry: 0Tx max lifetime exceeded: 0Tx ACK failure: 199Roaming history: 0 item(s)Time to start re-introducing variables, I think...Details about wireless connectivity diagnosis:For complete information about this session see the wireless connectivity information event.Helper Class: Auto ConfigurationInitialize status: SuccessInformation for connection being diagnosedInterface GUID: 125860e2-8019-475a-806c-2d553e9e8c8cInterface name: Qualcomm Atheros AR9485WB-EG Wireless Network AdapterInterface type: Native WiFiResult of diagnosis: There may be problemAfter I re-enabled the NPCap Loopback Interface, I started VMware Player, to see if I could reproduce BAD_POOL_CALLER, but as of 09:04pm, there's no crash.Bizarrely, starting VMware Player resulted in:I don't know if this is related to NPCap, though - but I could reproduce it, after re-launching Player. Curiously, I was able to begin starting a VM, before seeing the error again.Judging from the log file, it's trying to create a new file, somewhere, where it supposedly doesn't have permission to write to (C:\ProgramData\VMware); and it also produced a core dump file, whilst I'll examine, shortly. However, Wireshark didn't crash, and there's still no sign of a BSoD, despite capturing over 36000 packets, whilst composing this e-mail.I think this is a new record for stability, so far.Tyson.2015-08-01 20:50 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:...and if I start Wireshark in "Administrator Mode", without running under the debugger (it doesn't detect any interfaces, otherwise - but I don't know if it'll suddenly try to invoke NPF, and crash my machine, yet), it lists interfaces, and I can capture from them.After waiting about 5 minutes, staring at the pretty interface activity graphs on the Welcome screen, my WLAN connection suddenly fails (the interface is marked as "Limited"):C:\Users\tyson_000>ping google.comPing request could not find host google.com. Please check the name and try again.C:\Users\tyson_000>ping 192.168.1.1Pinging 192.168.1.1 with 32 bytes of data:Request timed out.Reply from 192.168.1.4: Destination host unreachable.Request timed out.Request timed out.Ping statistics for 192.168.1.1:Packets: Sent = 4, Received = 1, Lost = 3 (75% loss)If I try to disconnect, and reconnect, I see "Connection to the network is taking longer than usual", and I can see broadcast traffic, in Wireshark - but not send/receive unicast traffic; and in order to regain connectivity, I have to disable, and then re-enable my WLAN interface, and then run a connection diagnosis, in order to reset routing.I never thought that I'd say so, but annoyingly, it hasn't BSoD'd at all, so far - which feels like there's a Heisenbug at play. :(Tyson.2015-08-01 20:26 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Hmm, this is interesting...When I removed the old WinPCap, and installed the new NPCap, and then started Wireshark under WinDBG, immediately after, it didn't crash - but at the same time, it didn't detect any interfaces, either.However, when I rebooted, and tried to start Wireshark under WinDBG, I was able to capture packets from my WLAN adapter (using the Qt UI), and then stop capturing, and then quit the Qt UI, and start the GTK one (under WDBG), and capture from all interfaces, including the NPCap Loopback - at the cost of my Internet connection being knocked out, for some unknown reason:Pinging 192.168.1.1 with 32 bytes of data:PING: transmit failed. General failure.PING: transmit failed. General failure.PING: transmit failed. General failure.PING: transmit failed. General failure.Ping statistics for 192.168.1.1:Packets: Sent = 4, Received = 0, Lost = 4 (100% loss)In both cases, I didn't receive any BSoD, or general signs of slowness, or instability (although I didn't stress things hard, and only captured a total of about 3000 packets). (I haven't tried capturing without running Wireshark in the debugger, yet).This is what gets loaded:ModLoad: 00007ff8`5acc0000 00007ff8`5ace0000 C:\WINDOWS\SYSTEM32\CRYPTSP.dllModLoad: 00007ff8`5a8e0000 00007ff8`5a916000 C:\WINDOWS\system32\rsaenh.dllModLoad: 00007ff8`5af60000 00007ff8`5af86000 C:\WINDOWS\SYSTEM32\bcrypt.dllApplication "\??\C:\Program Files\Wireshark\gspawn-win64-helper.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheApplication "\??\C:\Program Files\Wireshark\dumpcap.exe" found in cacheModLoad: 00007ff8`5ad20000 00007ff8`5ad2c000 C:\WINDOWS\SYSTEM32\Secur32.dllModLoad: 00007ff8`5b270000 00007ff8`5b29e000 C:\WINDOWS\SYSTEM32\SSPICLI.DLLModLoad: 00007ff8`58d70000 00007ff8`58d7c000 C:\WINDOWS\SYSTEM32\ondemandconnroutehelper.dllModLoad: 00007ff8`53650000 00007ff8`53719000 C:\WINDOWS\SYSTEM32\winhttp.dllModLoad: 00007ff8`5a440000 00007ff8`5a4a2000 C:\windows\system32\nuragoLSPService64.DLLModLoad: 00007ff8`5ac60000 00007ff8`5acb9000 C:\WINDOWS\SYSTEM32\MSWSOCK.dllModLoad: 00007ff8`55e90000 00007ff8`55ea6000 C:\WINDOWS\SYSTEM32\dhcpcsvc6.DLLModLoad: 00007ff8`560a0000 00007ff8`560ba000 C:\WINDOWS\SYSTEM32\dhcpcsvc.DLLModLoad: 00007ff8`54e10000 00007ff8`54f95000 C:\WINDOWS\SYSTEM32\urlmon.dllModLoad: 00007ff8`52f70000 00007ff8`52f88000 C:\windows\system32\wlidnsp.dllModLoad: 00007ff8`59fd0000 00007ff8`59fda000 C:\WINDOWS\SYSTEM32\DPAPI.DLLModLoad: 00000000`65d50000 00000000`65d76000 C:\Program Files\Bonjour\mdnsNSP.dllModLoad: 00007ff8`52f60000 00007ff8`52f6a000 C:\Windows\System32\rasadhlp.dll(1ffc.2544): C++ EH exception - code e06d7363 (first chance)(1ffc.2544): C++ EH exception - code e06d7363 (first chance)(1ffc.2544): C++ EH exception - code e06d7363 (first chance)Unsure of why the Nurago/Gacela LSP is still being loaded, despite supposedly no longer being installed, though. In order to restore network connectivity, I had to disable the "NPcap Loopback Adapter", and a vestigial "KM-TEST Loopback Adaptor", and reboot my PC, though.Tyson.2015-08-01 17:22 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Also found this, in a dumpcap MiniDump:Microsoft (R) Windows Debugger Version 6.3.9600.17336 AMD64Copyright (c) Microsoft Corporation. All rights reserved.Loading Dump File [C:\MiniDumps\072715-31968-01.dmp]Mini Kernel Dump File: Only registers and stack trace are available************* Symbol Path validation summary **************Response Time (ms) LocationDeferred SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsSymbol search path is: SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsExecutable search path is:Windows 8 Kernel Version 9600 MP (4 procs) Free x64Product: WinNt, suite: TerminalServer SingleUserTS PersonalBuilt by: 9600.17736.amd64fre.winblue_r9.150322-1500Machine Name:Kernel base = 0xfffff801`0668c000 PsLoadedModuleList = 0xfffff801`06965850Debug session time: Mon Jul 27 19:02:32.113 2015 (UTC + 1:00)System Uptime: 0 days 0:15:05.990Loading Kernel Symbols.Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.Run !sym noisy before .reload to track down problems loading symbols.....................................................................................................................................................................................................Loading User SymbolsLoading unloaded module list.......................******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************Use !analyze -v to get detailed debugging information.BugCheck 3B, {c0000005, fffff8011be5d485, ffffd0002324e980, 0}*** WARNING: Unable to verify timestamp for npf.sys*** ERROR: Module load completed but symbols could not be loaded for npf.sysProbably caused by : npf.sys ( npf+26b9 )Followup: MachineOwner---------3: kd> !analyze -v******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************SYSTEM_SERVICE_EXCEPTION (3b)An exception happened while executing a system service routine.Arguments:Arg1: 00000000c0000005, Exception code that caused the bugcheckArg2: fffff8011be5d485, Address of the instruction which caused the bugcheckArg3: ffffd0002324e980, Address of the context record for the exception that caused the bugcheckArg4: 0000000000000000, zero.Debugging Details:------------------EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.FAULTING_IP:ndis!NdisFOidRequest+79fffff801`1be5d485 4883b80001000000 cmp qword ptr [rax+100h],0CONTEXT: ffffd0002324e980 -- (.cxr 0xffffd0002324e980;r)rax=0000000000026799 rbx=ffffe00015dd60c0 rcx=ffffe00017b809e0rdx=ffffe00015dd60c0 rsi=00000000c0000001 rdi=ffffe00017b809e0rip=fffff8011be5d485 rsp=ffffd0002324f3b0 rbp=ffffe00015dd6070r8=0000000000000000 r9=0000000000000000 r10=0000000000000801r11=ffffd0002324f420 r12=ffffe000161aac90 r13=ffffe000174edd90r14=ffffe00015dd60c0 r15=ffffe00015dd6078iopl=0 nv up ei pl zr na po nccs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010246ndis!NdisFOidRequest+0x79:fffff801`1be5d485 4883b80001000000 cmp qword ptr [rax+100h],0 ds:002b:00000000`00026899=????????????????Last set context:rax=0000000000026799 rbx=ffffe00015dd60c0 rcx=ffffe00017b809e0rdx=ffffe00015dd60c0 rsi=00000000c0000001 rdi=ffffe00017b809e0rip=fffff8011be5d485 rsp=ffffd0002324f3b0 rbp=ffffe00015dd6070r8=0000000000000000 r9=0000000000000000 r10=0000000000000801r11=ffffd0002324f420 r12=ffffe000161aac90 r13=ffffe000174edd90r14=ffffe00015dd60c0 r15=ffffe00015dd6078iopl=0 nv up ei pl zr na po nccs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010246ndis!NdisFOidRequest+0x79:fffff801`1be5d485 4883b80001000000 cmp qword ptr [rax+100h],0 ds:002b:00000000`00026899=????????????????Resetting default scopeCUSTOMER_CRASH_COUNT: 1DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULTBUGCHECK_STR: 0x3BPROCESS_NAME: dumpcap.exeCURRENT_IRQL: 0ANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) amd64freLAST_CONTROL_TRANSFER: from fffff8011cb606b9 to fffff8011be5d485STACK_TEXT:ffffd000`2324f3b0 fffff801`1cb606b9 : ffffe000`15dd6098 ffffe000`15dd6000 ffffe000`15dd6098 ffffe000`15dd6000 : ndis!NdisFOidRequest+0x79ffffd000`2324f470 ffffe000`15dd6098 : ffffe000`15dd6000 ffffe000`15dd6098 ffffe000`15dd6000 ffffe000`161aad28 : npf+0x26b9ffffd000`2324f478 ffffe000`15dd6000 : ffffe000`15dd6098 ffffe000`15dd6000 ffffe000`161aad28 ffffe000`1a182210 : 0xffffe000`15dd6098ffffd000`2324f480 ffffe000`15dd6098 : ffffe000`15dd6000 ffffe000`161aad28 ffffe000`1a182210 ffffe000`161aac90 : 0xffffe000`15dd6000ffffd000`2324f488 ffffe000`15dd6000 : ffffe000`161aad28 ffffe000`1a182210 ffffe000`161aac90 fffff801`1cb609c0 : 0xffffe000`15dd6098ffffd000`2324f490 ffffe000`161aad28 : ffffe000`1a182210 ffffe000`161aac90 fffff801`1cb609c0 ffffe000`16c102e0 : 0xffffe000`15dd6000ffffd000`2324f498 ffffe000`1a182210 : ffffe000`161aac90 fffff801`1cb609c0 ffffe000`16c102e0 ffffe000`16c103b0 : 0xffffe000`161aad28ffffd000`2324f4a0 ffffe000`161aac90 : fffff801`1cb609c0 ffffe000`16c102e0 ffffe000`16c103b0 ffffe000`15dd6000 : 0xffffe000`1a182210ffffd000`2324f4a8 fffff801`1cb609c0 : ffffe000`16c102e0 ffffe000`16c103b0 ffffe000`15dd6000 ffffe000`174edee0 : 0xffffe000`161aac90ffffd000`2324f4b0 ffffe000`16c102e0 : ffffe000`16c103b0 ffffe000`15dd6000 ffffe000`174edee0 ffffe000`16c102e0 : npf+0x29c0ffffd000`2324f4b8 ffffe000`16c103b0 : ffffe000`15dd6000 ffffe000`174edee0 ffffe000`16c102e0 fffff801`06aaedd1 : 0xffffe000`16c102e0ffffd000`2324f4c0 ffffe000`15dd6000 : ffffe000`174edee0 ffffe000`16c102e0 fffff801`06aaedd1 00000000`000000a5 : 0xffffe000`16c103b0ffffd000`2324f4c8 ffffe000`174edee0 : ffffe000`16c102e0 fffff801`06aaedd1 00000000`000000a5 ffffd000`2324f7e1 : 0xffffe000`15dd6000ffffd000`2324f4d0 ffffe000`16c102e0 : fffff801`06aaedd1 00000000`000000a5 ffffd000`2324f7e1 00000000`00000000 : 0xffffe000`174edee0ffffd000`2324f4d8 fffff801`06aaedd1 : 00000000`000000a5 ffffd000`2324f7e1 00000000`00000000 00000000`00000040 : 0xffffe000`16c102e0ffffd000`2324f4e0 fffff801`06b35dc4 : 00000000`00000000 00000000`00000000 ffffe000`174edd60 ffffe000`174edd60 : nt!IopParseDevice+0x6c1ffffd000`2324f700 fffff801`06ac36b3 : 00000000`00000000 ffffd000`2324f8a8 00000000`00000040 ffffe000`153eca90 : nt!ObpLookupObjectName+0x784ffffd000`2324f830 fffff801`06adc4db : 00000000`00000001 ffffe000`1a1822a8 00000000`00000001 00000000`00000020 : nt!ObOpenObjectByName+0x1e3ffffd000`2324f960 fffff801`06adc15c : 00000017`feefcbb8 00000000`c0100080 00000017`feefcc10 ffffe000`1646e080 : nt!IopCreateFile+0x36bffffd000`2324fa00 fffff801`067e84b3 : ffffe000`1a537080 ffffd000`2324fb80 ffffd000`2324faa8 00000017`feefcb60 : nt!NtCreateFile+0x78ffffd000`2324fa90 00007ff8`1110171a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x1300000017`feefcb38 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`1110171aFOLLOWUP_IP:npf+26b9fffff801`1cb606b9 ?? ???SYMBOL_STACK_INDEX: 1SYMBOL_NAME: npf+26b9FOLLOWUP_NAME: MachineOwnerMODULE_NAME: npfIMAGE_NAME: npf.sysDEBUG_FLR_IMAGE_TIMESTAMP: 55b5ffcdSTACK_COMMAND: .cxr 0xffffd0002324e980 ; kbFAILURE_BUCKET_ID: 0x3B_npf+26b9BUCKET_ID: 0x3B_npf+26b9ANALYSIS_SOURCE: KMFAILURE_ID_HASH_STRING: km:0x3b_npf+26b9FAILURE_ID_HASH: {3d7b38a9-fc4b-1ac1-803d-31b7fb0e6e7f}Followup: MachineOwner---------2015-08-01 16:07 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Hi Yang,Not sure if these are any use, since I'm still downloading various symbols, but I've just started looking at some MiniDumps, and spotted these:Microsoft (R) Windows Debugger Version 6.3.9600.17336 AMD64Copyright (c) Microsoft Corporation. All rights reserved.Loading Dump File [C:\Windows\Minidump\072715-48062-01.dmp]Mini Kernel Dump File: Only registers and stack trace are available************* Symbol Path validation summary **************Response Time (ms) LocationDeferred SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsSymbol search path is: SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsExecutable search path is:Windows 8 Kernel Version 9600 MP (4 procs) Free x64Product: WinNt, suite: TerminalServer SingleUserTS PersonalBuilt by: 9600.17736.amd64fre.winblue_r9.150322-1500Machine Name:Kernel base = 0xfffff801`03606000 PsLoadedModuleList = 0xfffff801`038df850Debug session time: Mon Jul 27 17:00:25.098 2015 (UTC + 1:00)System Uptime: 0 days 0:49:51.971Loading Kernel Symbols.Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.Run !sym noisy before .reload to track down problems loading symbols.....................................................................................................................................................................................................Loading User SymbolsLoading unloaded module list......................******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************Use !analyze -v to get detailed debugging information.BugCheck C2, {7, 1200, 0, ffffe0004bc1b4c8}GetPointerFromAddress: unable to read from fffff80103969138unable to get nt!MmNonPagedPoolStartunable to get nt!MmSizeOfNonPagedPoolInBytesProbably caused by : NETIO.SYS ( NETIO!NetioCompleteCloneNetBufferListChain+1508d )Followup: MachineOwner---------0: kd> !analyze -v******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************BAD_POOL_CALLER (c2)The current thread is making a bad pool request. Typically this is at a bad IRQL level or double freeing the same allocation, etc.Arguments:Arg1: 0000000000000007, Attempt to free pool which was already freedArg2: 0000000000001200, (reserved)Arg3: 0000000000000000, Memory contents of the pool blockArg4: ffffe0004bc1b4c8, Address of the block of pool being deallocatedDebugging Details:------------------POOL_ADDRESS: ffffe0004bc1b4c8FREED_POOL_TAG: NDndBUGCHECK_STR: 0xc2_7_NDndCUSTOMER_CRASH_COUNT: 1DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULTPROCESS_NAME: Asset-uPNP.exeCURRENT_IRQL: 2ANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) amd64freLAST_CONTROL_TRANSFER: from fffff801038aaff2 to fffff80103756ca0STACK_TEXT:ffffd000`5e10ef88 fffff801`038aaff2 : 00000000`000000c2 00000000`00000007 00000000`00001200 00000000`00000000 : nt!KeBugCheckExffffd000`5e10ef90 fffff800`7482f83d : 00000000`00000000 ffffe000`47728040 000008fe`00000010 00000014`00000000 : nt!ExAllocatePoolWithTag+0x1102ffffd000`5e10f080 fffff800`748013f1 : 00000000`00000000 ffffe000`46f0a250 00000000`00000000 00000000`00000000 : NETIO!NetioCompleteCloneNetBufferListChain+0x1508dffffd000`5e10f0f0 fffff800`74d28c18 : fffff800`74866228 00000000`00000001 00000000`00000000 00000000`00000000 : NETIO!NetioDereferenceNetBufferListChain+0x2d1ffffd000`5e10f190 fffff800`74cfe18c : ffffe000`4b554b7c 00000000`000490ce 00000000`00000000 00000000`00000000 : tcpip!TcpFlushDelay+0x88ffffd000`5e10f240 fffff800`74d33f9f : ffffe000`476c8940 ffffd000`5e100d66 ffffd000`5e1087c2 ffffe000`477287c2 : tcpip!TcpPreValidatedReceive+0x3ccffffd000`5e10f340 fffff800`74d30143 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!IppDeliverListToProtocol+0x4fffffd000`5e10f400 fffff800`74d2e525 : 00000000`00000000 00000000`00000000 00000000`00000000 ffffd000`5e10f508 : tcpip!IppProcessDeliverList+0x63ffffd000`5e10f4a0 fffff800`74ce6c9d : 00000000`00000000 00000000`00000000 00000000`00000000 ffffd000`5e10f6b8 : tcpip!IppReceiveHeaderBatch+0x235ffffd000`5e10f5d0 fffff800`74ce61cc : ffffd000`5e10f6e0 00000000`00000000 ffffe000`49cc7040 ffffd000`5e10f820 : tcpip!IppLoopbackIndicatePackets+0x39dffffd000`5e10f6b0 fffff800`74d03eb8 : ffffe000`4cd20190 346dc5d6`38865900 ffffd000`5e10f8e0 00000000`00000000 : tcpip!IppLoopbackEnqueue+0x3dcffffd000`5e10f7e0 fffff800`74d03389 : fffff800`74e7e180 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!IppDispatchSendPacketHelper+0x398ffffd000`5e10f970 fffff800`74d0191e : ffff0014`00000001 ffffe000`4769bb28 00000000`00000002 ffffd000`5e10fdc0 : tcpip!IppPacketizeDatagrams+0x2d9ffffd000`5e10fb10 fffff800`74d06ab7 : fffff800`74cc74f0 00000000`00000007 fffff800`74e7e180 ffffe000`4ce29010 : tcpip!IppSendDatagramsCommon+0x49effffd000`5e10fcf0 fffff800`74cfc435 : ffffd000`5e1100d2 00000000`00000000 ffffe000`48afd280 ffffd000`5e1103f0 : tcpip!TcpTcbSend+0x55bffffd000`5e110040 fffff800`74cfc07c : 00000000`000490ce ffffe000`4ce29010 ffffd000`5e1100d1 ffffd000`5e110300 : tcpip!TcpEnqueueTcbSendOlmNotifySendComplete+0xa5ffffd000`5e110070 fffff800`74cfc538 : 00000000`00000000 00000000`00000000 ffffe000`4b563500 00000000`00000000 : tcpip!TcpEnqueueTcbSend+0x2acffffd000`5e110170 fffff801`03678703 : 00000000`00000000 00000000`00000001 00000000`00000000 00000000`00000000 : tcpip!TcpTlConnectionSendCalloutRoutine+0x28ffffd000`5e1101f0 fffff800`74cfc7f6 : fffff800`74cfc510 ffffd000`5e110310 ffffe000`4bf7a600 fffff800`7572d7ab : nt!KeExpandKernelStackAndCalloutInternal+0xf3ffffd000`5e1102e0 fffff800`75747b97 : ffffe000`4b563560 ffffd000`5e110b80 00000000`00000a71 00000000`000000b8 : tcpip!TcpTlConnectionSend+0x76ffffd000`5e110350 fffff800`7572c450 : ffffe000`4bd1cc30 00000000`00000000 00000000`00000000 00000000`00000001 : afd!AfdFastConnectionSend+0x387ffffd000`5e110510 fffff801`03a2b27c : 00000000`00000000 ffffe000`470358d0 ffffe000`478442e0 00000000`00000001 : afd!AfdFastIoDeviceControl+0x440ffffd000`5e110880 fffff801`03a2ad22 : ffffe000`4cb3f880 0000000c`001f0003 00000000`00000001 00000000`00000000 : nt!IopXxxControlFile+0x54cffffd000`5e110a20 fffff801`037624b3 : fffff6fb`7dbed000 fffff6fb`7da00000 fffff6fb`40000098 fffff680`00013438 : nt!NtDeviceIoControlFile+0x56ffffd000`5e110a90 00000000`76f32352 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x1300000000`01ecf128 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x76f32352STACK_COMMAND: kbFOLLOWUP_IP:NETIO!NetioCompleteCloneNetBufferListChain+1508dfffff800`7482f83d 90 nopSYMBOL_STACK_INDEX: 2SYMBOL_NAME: NETIO!NetioCompleteCloneNetBufferListChain+1508dFOLLOWUP_NAME: MachineOwnerMODULE_NAME: NETIOIMAGE_NAME: NETIO.SYSDEBUG_FLR_IMAGE_TIMESTAMP: 540ebbe6IMAGE_VERSION: 6.3.9600.17337BUCKET_ID_FUNC_OFFSET: 1508dFAILURE_BUCKET_ID: 0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChainBUCKET_ID: 0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChainANALYSIS_SOURCE: KMFAILURE_ID_HASH_STRING: km:0xc2_7_ndnd_netio!netiocompleteclonenetbufferlistchainFAILURE_ID_HASH: {ec09700b-3916-f849-b5d5-75c2ba7b02db}Followup: MachineOwner---------Microsoft (R) Windows Debugger Version 6.3.9600.17336 AMD64Copyright (c) Microsoft Corporation. All rights reserved.Loading Dump File [C:\Windows\Minidump\072815-328875-01.dmp]Mini Kernel Dump File: Only registers and stack trace are available************* Symbol Path validation summary **************Response Time (ms) LocationDeferred SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsSymbol search path is: SRV*C:\Symbols\*http://msdl.microsoft.com/download/symbolsExecutable search path is:Windows 8 Kernel Version 9600 MP (4 procs) Free x64Product: WinNt, suite: TerminalServer SingleUserTS PersonalBuilt by: 9600.17736.amd64fre.winblue_r9.150322-1500Machine Name:Kernel base = 0xfffff800`0ce07000 PsLoadedModuleList = 0xfffff800`0d0e0850Debug session time: Tue Jul 28 16:30:31.391 2015 (UTC + 1:00)System Uptime: 0 days 0:07:03.265Loading Kernel Symbols.Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.Run !sym noisy before .reload to track down problems loading symbols.............................................................................................................................................................................................Loading User SymbolsLoading unloaded module list....................******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************Use !analyze -v to get detailed debugging information.BugCheck C2, {7, 1200, 117ec1, ffffe0015aeeaec8}GetPointerFromAddress: unable to read from fffff8000d16a138unable to get nt!MmNonPagedPoolStartunable to get nt!MmSizeOfNonPagedPoolInBytesProbably caused by : NETIO.SYS ( NETIO!NetioCompleteCloneNetBufferListChain+1508d )Followup: MachineOwner---------2: kd> !analyze -v******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************BAD_POOL_CALLER (c2)The current thread is making a bad pool request. Typically this is at a bad IRQL level or double freeing the same allocation, etc.Arguments:Arg1: 0000000000000007, Attempt to free pool which was already freedArg2: 0000000000001200, (reserved)Arg3: 0000000000117ec1, Memory contents of the pool blockArg4: ffffe0015aeeaec8, Address of the block of pool being deallocatedDebugging Details:------------------POOL_ADDRESS: ffffe0015aeeaec8FREED_POOL_TAG: NDndBUGCHECK_STR: 0xc2_7_NDndCUSTOMER_CRASH_COUNT: 1DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULTPROCESS_NAME: svchost.exeCURRENT_IRQL: 2ANALYSIS_VERSION: 6.3.9600.17336 (debuggers(dbg).150226-1500) amd64freLAST_CONTROL_TRANSFER: from fffff8000d0abff2 to fffff8000cf57ca0STACK_TEXT:ffffd000`9bba4ba8 fffff800`0d0abff2 : 00000000`000000c2 00000000`00000007 00000000`00001200 00000000`00117ec1 : nt!KeBugCheckExffffd000`9bba4bb0 fffff801`14a2f83d : 00000000`00000000 ffffe001`5a593040 000008fe`00000010 00000014`00000011 : nt!ExAllocatePoolWithTag+0x1102ffffd000`9bba4ca0 fffff801`14a013f1 : 00000000`00000000 ffffe001`59b5b600 00000000`00000000 00000000`00000000 : NETIO!NetioCompleteCloneNetBufferListChain+0x1508dffffd000`9bba4d10 fffff801`14d2bc18 : fffff801`14a66228 00000000`00000001 00000000`00000000 00000000`00000000 : NETIO!NetioDereferenceNetBufferListChain+0x2d1ffffd000`9bba4db0 fffff801`14d0118c : ffffe001`5de21fcc 00000000`0000a567 00000000`00000000 00000000`00000000 : tcpip!TcpFlushDelay+0x88ffffd000`9bba4e60 fffff801`14d36f9f : ffffe001`5a527d80 ffffd000`9bba350b ffffd000`9bba81c1 ffffe001`5a4f81c1 : tcpip!TcpPreValidatedReceive+0x3ccffffd000`9bba4f60 fffff801`14d33143 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!IppDeliverListToProtocol+0x4fffffd000`9bba5020 fffff801`14d31525 : 00000000`00000000 00000000`00000000 00000000`00000000 ffffd000`9bba5128 : tcpip!IppProcessDeliverList+0x63ffffd000`9bba50c0 fffff801`14ce9c9d : 00000000`00000000 00000000`00000000 00000000`00000000 ffffd000`9bba52d8 : tcpip!IppReceiveHeaderBatch+0x235ffffd000`9bba51f0 fffff801`14ce91cc : ffffd000`9bba5300 00000000`00000000 ffffe001`5cdfa540 ffffd000`9bba5440 : tcpip!IppLoopbackIndicatePackets+0x39dffffd000`9bba52d0 fffff801`14d06eb8 : ffffe001`59e84600 346dc5d6`38865900 ffffd000`9bba5500 00000000`00000000 : tcpip!IppLoopbackEnqueue+0x3dcffffd000`9bba5400 fffff801`14d06389 : fffff801`14e81180 00000000`00000000 00000000`00000000 00000000`00000000 : tcpip!IppDispatchSendPacketHelper+0x398ffffd000`9bba5590 fffff801`14d0491e : ffff0014`00000001 ffffe001`5a4bc568 00000000`00000002 ffffd000`9bba59e0 : tcpip!IppPacketizeDatagrams+0x2d9ffffd000`9bba5730 fffff801`14d09ab7 : fffff801`14cca4f0 00000000`00000007 fffff801`14e81180 ffffe001`5c76f8c0 : tcpip!IppSendDatagramsCommon+0x49effffd000`9bba5910 fffff801`14cff435 : ffffd000`9bba5cf2 00000000`00000000 ffffe001`5caff550 ffffd000`9bba5f90 : tcpip!TcpTcbSend+0x55bffffd000`9bba5c60 fffff801`14cff07c : 00000000`0000a567 ffffe001`5c76f8c0 ffffd000`9bba5cf1 ffffd000`9bba5f00 : tcpip!TcpEnqueueTcbSendOlmNotifySendComplete+0xa5ffffd000`9bba5c90 fffff801`14cff538 : ffffc001`5b0b1b02 00000000`00000000 ffffe001`5dbf5100 00000000`0ce5a000 : tcpip!TcpEnqueueTcbSend+0x2acffffd000`9bba5d90 fffff800`0ce79703 : ffffe001`5dbf51e0 fffff801`14cff7f6 fffff801`14cff510 ffffd000`9bba5e50 : tcpip!TcpTlConnectionSendCalloutRoutine+0x28ffffd000`9bba5e10 fffff801`14cff7f6 : fffff801`14cff510 ffffd000`9bba5f30 ffffc001`5b0b1e00 00000000`00000000 : nt!KeExpandKernelStackAndCalloutInternal+0xf3ffffd000`9bba5f00 fffff801`15402ecf : ffffe001`5dbf51e0 ffffe001`59f3c4c0 00000000`00000000 ffffe001`5db660c0 : tcpip!TcpTlConnectionSend+0x76ffffd000`9bba5f70 fffff801`184e7860 : ffffe001`5c7b9cb0 00000000`00000002 ffffe001`5db660c0 ffffe001`5c75b050 : afd!WskProIRPSend+0xbfffffd000`9bba5fe0 fffff801`184e647c : 00000000`ffffffff ffffe001`59fc96f8 00000580`00000000 fffffa80`001ca790 : HTTP!UxTlInitiateSend+0x1e0ffffd000`9bba60a0 fffff801`1855b0ea : ffffe001`59fc96f8 00000000`00000000 00000000`00000001 00000000`00000000 : HTTP!UxpTpFastTransmit+0x19cffffd000`9bba6140 fffff801`184e7cad : ffffe001`59fc9420 fffff801`184e64ff 00000000`00000000 ffffe001`58ef53b0 : HTTP!UxTpTransmitPacket+0xbaffffd000`9bba61e0 fffff801`18559bbf : 00000000`00000000 00000000`00000000 fffff801`18536ae0 ffffe001`58ef53b0 : HTTP!UlSendData+0xddffffd000`9bba6270 fffff801`18574a7f : 00000000`00000000 fffff801`18536ae0 ffffe001`5a211850 ffffe001`5a211850 : HTTP!UlFastSendHttpResponse+0x1765ffffd000`9bba6500 fffff801`184e42b8 : 00000000`00124043 fffff801`1854c180 00000000`00000020 ffffe001`5a2119f8 : HTTP!UlSendEntityBodyIoctl+0xd2fffffd000`9bba6840 fffff800`0d22c77f : 00000000`00000000 ffffd000`9bba6b80 ffffe001`5a211850 00000000`00000004 : HTTP!UlDeviceControl+0x78ffffd000`9bba6880 fffff800`0d22bd22 : ffffd000`9bba6a38 00000000`00000000 00000000`00000000 00000000`00000000 : nt!IopXxxControlFile+0xa4fffffd000`9bba6a20 fffff800`0cf634b3 : ffffe001`58edf080 00000000`001f0003 00000031`01acf0f8 00000000`00000001 : nt!NtDeviceIoControlFile+0x56ffffd000`9bba6a90 00007ff8`24c3123a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x1300000031`01ace928 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`24c3123aSTACK_COMMAND: kbFOLLOWUP_IP:NETIO!NetioCompleteCloneNetBufferListChain+1508dfffff801`14a2f83d 90 nopSYMBOL_STACK_INDEX: 2SYMBOL_NAME: NETIO!NetioCompleteCloneNetBufferListChain+1508dFOLLOWUP_NAME: MachineOwnerMODULE_NAME: NETIOIMAGE_NAME: NETIO.SYSDEBUG_FLR_IMAGE_TIMESTAMP: 540ebbe6IMAGE_VERSION: 6.3.9600.17337BUCKET_ID_FUNC_OFFSET: 1508dFAILURE_BUCKET_ID: 0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChainBUCKET_ID: 0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChainANALYSIS_SOURCE: KMFAILURE_ID_HASH_STRING: km:0xc2_7_ndnd_netio!netiocompleteclonenetbufferlistchainFAILURE_ID_HASH: {ec09700b-3916-f849-b5d5-75c2ba7b02db}Followup: MachineOwner---------However, they seem to correlate with your debugging from earlier...Tyson.2015-08-01 14:30 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Hi Yang,Thanks for looking at this. I've just enabled full memory dumps, after reading https://support.microsoft.com/en-us/kb/969028 - but I'll need to do the Right Ctrl + Scroll Lock X2 trick at a time when I can afford to lose state data.I've got the Windows SDK installed (but not the WinDBG?), if I remember correctly - but I'll install the symbols, and WDK, when I get time. In the meantime, since I've got a %SystemRoot%\MEMORY.DMP file from some crash, but don't know how big it is (since I now have 6GB of RAM, and probably only had 4GB, when it was generated - assuming that "automatic" dumps are "full" dumps), I guess that I've got something to practice post-mortem on...Tyson.2015-08-01 4:18 GMT+01:00 Yang Luo <hsluoyb@xxxxxxxxx>:Hi Tyson,I think I have reproduced the BAD_POOL_CALLER error, the step is: 1) reboot the system, 2) start Wireshark UI, 3) Open VMware Workstation. As you installed VMware Player, maybe it's the same reason. I will look into this later. And I found that a full dump file (memory.dmp) has more useful information (the error position in Npcap driver) than a minidump, so if you can provide full dumps, it will be better. A simpler way is you open the full dump file by yourself using WinDBG (with suitable symbols) and type in "!analyze -v", and then paste the output in this thread, so you don't need to upload such a big dump file.Get WinDBG:Get Windows symbols:Cheers,YangOn Tue, Jul 28, 2015 at 11:09 PM, Tyson Key <tyson.key@xxxxxxxxx> wrote:Aah, I had a look at "Programs, and Features", and it says that the AppEx thing is "AMD Quick Stream" 3.4.4.0, published by AppEx Networks, of Beijing (http://www.appexnetworks.com.cn/). I found a marketing document regarding it at http://support.amd.com/en-us/kb-articles/Pages/AMDQuickStreamTechnology.aspx.Tyson.2015-07-28 16:03 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Hi Yang,Thanks for looking at these dumps.Yup, I think I enabled the verifier, a few months ago, whilst trying to debug some other issue (probably related to the AppEx thing), and I forgot that I kept it enabled.As for the dumpcap arguments, I just let Wireshark invoke it, through the GUI - so the arguments are whatever it spits out by default, to set up various pipes. I'd have to surgically remove NPCap, and replace it with regular WinPCap, and then try to trace Wireshark Qt/GTK, to learn the arguments (or see if "tasklist /V", or some other utility reveals them). I'd expect that they'd look similar to the ones issued under Linux, modulo device names, though.I'm kinda surprised that Asset is responsible for some of the crashes, to be honest. Sure, it does funny things with multicasting, as a UPnP server implementation, but it's usually pretty reliable, in general operation. Might be worth me reporting a bug to Illustrate, when I get chance; and I'll see what happens if I uninstall it, in the meantime.As for AppEx, I'm pretty sure that I removed its driver from all of my interfaces, but I wouldn't be surprised if there's not something vestigial. Going to see if I can fully cleanse it from my system, since it was an OEM-supplied product, and not something that I opted to install. (And I've had BSoDs from it before, whilst trying to diagnose some WLAN problems). I think it's supposed to be some sort of "game/multimedia quality-of-service optimisation" tool.Take care,Tyson.2015-07-28 12:41 GMT+01:00 Yang Luo <hsluoyb@xxxxxxxxx>:Hi Tyson,I have analyzed the five dumps you provided:1) 072715-32078-01.dmpThis dump is caused by nt!VerifierBugCheckIfAppropriate+0x3c code from process svchost.exe, and it seems to be that you switched on Verifier function for your system. I think there's no relationship with Npcap.2) 072715-31968-01.dmp and 072715-32468-01.dmpthis dump provides BSoD about SYSTEM_SERVICE_EXCEPTION. It is caused by ndis!NdisFOidRequest+62 code from process dumpcap.exe. As Npcap uses NdisFOidRequest calls, I think it's possibly a bug. I'd like to know how you used dumpcap.exe, like parameters?3) 072715-33859-01.dmp and 072715-48062-01.dmpIt is caused by Asset-uPNP.exe, from Asset audio server software provided by illustrate. I think maybe you would like to disable or uninstall it first, to see if the fault still happens. WinDbg also reports that OVERLAPPED_MODULE: Address regions for 'nwifi' and 'appexDrv.sys' overlap. 'appexDrv.sys''s description is " "AppEx Accelerator LWF/WFP Driver L.E."". nwifi.sys seems to be a Microsoft built-in component, and AppEx Networks Accelerator seems to be a VPN software, unfortunately, I didn't find a download link. But this is maybe not the main cause, whatever you can try to shutdown it to see if there's any change.072715-48062-01.dmp's report is pasted here:******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************Use !analyze -v to get detailed debugging information.BugCheck C2, {7, 1200, 0, ffffe0008d01cbf8}fffff80059152240: Unable to get special pool infofffff80059152240: Unable to get special pool infounable to get nt!MmPoolCodeStartunable to get nt!MmPoolCodeEndProbably caused by : NETIO.SYS ( NETIO!NetioCompleteCloneNetBufferListChain+1508d )Followup: MachineOwner---------0: kd> !analyze -v******************************************************************************** ** Bugcheck Analysis ** ********************************************************************************BAD_POOL_CALLER (c2)The current thread is making a bad pool request. Typically this is at a bad IRQL level or double freeing the same allocation, etc.Arguments:Arg1: 0000000000000007, Attempt to free pool which was already freedArg2: 0000000000001200, (reserved)Arg3: 0000000000000000, Memory contents of the pool blockArg4: ffffe0008d01cbf8, Address of the block of pool being deallocatedDebugging Details:------------------OVERLAPPED_MODULE: Address regions for 'nwifi' and 'appexDrv.sys' overlapPOOL_ADDRESS: ffffe0008d01cbf8FREED_POOL_TAG: NDndBUGCHECK_STR: 0xc2_7_NDndCUSTOMER_CRASH_COUNT: 1DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULTPROCESS_NAME: Asset-uPNP.exeCURRENT_IRQL: 2LAST_CONTROL_TRANSFER: from fffff8005912fff2 to fffff80058fdbca0STACK_TEXT:ffffd000`27118f88 fffff800`5912fff2 : 00000000`000000c2 00000000`00000007 00000000`00001200 00000000`00000000 : nt!KeBugCheckExffffd000`27118f90 fffff800`3763083d : 00000000`00000000 ffffe000`8d596040 000008fe`00000010 00000014`00000000 : nt!ExAllocatePoolWithTag+0x1102ffffd000`27119080 fffff800`376023f1 : 00000000`00000000 ffffe000`8ceb3740 00000000`00000000 00000000`00000000 : NETIO!NetioCompleteCloneNetBufferListChain+0x1508dffffd000`271190f0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : NETIO!NetioDereferenceNetBufferListChain+0x2d1STACK_COMMAND: kbFOLLOWUP_IP:NETIO!NetioCompleteCloneNetBufferListChain+1508dfffff800`3763083d 90 nopSYMBOL_STACK_INDEX: 2SYMBOL_NAME: NETIO!NetioCompleteCloneNetBufferListChain+1508dFOLLOWUP_NAME: MachineOwnerMODULE_NAME: NETIOIMAGE_NAME: NETIO.SYSDEBUG_FLR_IMAGE_TIMESTAMP: 540ebbe6FAILURE_BUCKET_ID: X64_0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChain+1508dBUCKET_ID: X64_0xc2_7_NDnd_NETIO!NetioCompleteCloneNetBufferListChain+1508dFollowup: MachineOwner---------On Tue, Jul 28, 2015 at 3:12 PM, Tyson Key <tyson.key@xxxxxxxxx> wrote:I just uploaded my MiniDumps to https://dl.dropboxusercontent.com/u/670345/MiniDump.rar, if it makes debugging this easier.Tyson.2015-07-28 8:08 GMT+01:00 Tyson Key <tyson.key@xxxxxxxxx>:Hi Yang,Thanks for looking into this.I can't remember when/how I installed Win10PCap (guessing that I briefly had a look, but couldn't get it to do anything on my machine, and just removed it), but I'm using VMware Player 6.0.7 build-2844087 (haven't got Workstation/Server installed); and I tried a dance of upgrading/downgrading/upgrading my AR9485WB-EG WLAN driver (first by downloading the package from http://support.lenovo.com/us/en/downloads/ds032333, to take me from 10.0.0.242, to 10.0.0.75; and then using Device Manager's driver update function, to take me to 3.0.1.155 (which I'm guessing is probably older than 242 - I'm just guessing from the sketchy build dates) - which gave me a different type of BSoD, initially, after starting Wireshark, but let me capture traffic for a little while, after rebooting.Here's all of the MiniDump summaries that I could find:==================================================Dump File : 072715-31968-01.dmpCrash Time : 27/07/2015 07:02:32 pmBug Check String : SYSTEM_SERVICE_EXCEPTIONBug Check Code : 0x0000003bParameter 1 : 00000000`c0000005Parameter 2 : fffff801`1be5d485Parameter 3 : ffffd000`2324e980Parameter 4 : 00000000`00000000Caused By Driver : ntoskrnl.exeCaused By Address : ntoskrnl.exe+150ca0File Description : NT Kernel & SystemProduct Name : Microsoft® Windows® Operating SystemCompany : Microsoft CorporationFile Version : 6.3.9600.17736 (winblue_r9.150322-1500)Processor : x64Crash Address : ntoskrnl.exe+150ca0Stack Address 1 :Stack Address 2 :Stack Address 3 :Computer Name :Full Path : C:\WINDOWS\Minidump\072715-31968-01.dmpProcessors Count : 4Major Version : 15Minor Version : 9600Dump File Size : 281,520Dump File Time : 27/07/2015 07:03:33 pm====================================================================================================Dump File : 072715-32078-01.dmpCrash Time : 27/07/2015 06:47:01 pmBug Check String : BAD_POOL_CALLERBug Check Code : 0x000000c2Parameter 1 : 00000000`00000099Parameter 2 : ffffe000`7d4b31b8Parameter 3 : 00000000`00000000Parameter 4 : 00000000`00000000Caused By Driver : tcpip.sysCaused By Address : tcpip.sys+42856File Description : TCP/IP DriverProduct Name : Microsoft® Windows® Operating SystemCompany : Microsoft CorporationFile Version : 6.3.9600.16384 (winblue_rtm.130821-1623)Processor : x64Crash Address : ntoskrnl.exe+150ca0Stack Address 1 :Stack Address 2 :Stack Address 3 :Computer Name :Full Path : C:\WINDOWS\Minidump\072715-32078-01.dmpProcessors Count : 4Major Version : 15Minor Version : 9600Dump File Size : 281,520Dump File Time : 27/07/2015 06:48:04 pm====================================================================================================Dump File : 072715-32468-01.dmpCrash Time : 27/07/2015 06:34:37 pmBug Check String : SYSTEM_SERVICE_EXCEPTIONBug Check Code : 0x0000003bParameter 1 : 00000000`c0000005Parameter 2 : fffff801`962a446eParameter 3 : ffffd001`1bd0f980Parameter 4 : 00000000`00000000Caused By Driver : ndis.sysCaused By Address : ndis.sys+546eFile Description : Network Driver Interface Specification (NDIS)Product Name : Microsoft® Windows® Operating SystemCompany : Microsoft CorporationFile Version : 6.3.9600.16384 (winblue_rtm.130821-1623)Processor : x64Crash Address : ntoskrnl.exe+150ca0Stack Address 1 :Stack Address 2 :Stack Address 3 :Computer Name :Full Path : C:\WINDOWS\Minidump\072715-32468-01.dmpProcessors Count : 4Major Version : 15Minor Version : 9600Dump File Size : 281,520Dump File Time : 27/07/2015 06:35:48 pm====================================================================================================Dump File : 072715-33859-01.dmpCrash Time : 27/07/2015 05:11:25 pmBug Check String : BAD_POOL_CALLERBug Check Code : 0x000000c2Parameter 1 : 00000000`00000007Parameter 2 : 00000000`00001200Parameter 3 : 00000000`00000000Parameter 4 : ffffe000`8d01cbf8Caused By Driver : ntoskrnl.exeCaused By Address : ntoskrnl.exe+150ca0File Description : NT Kernel & SystemProduct Name : Microsoft® Windows® Operating SystemCompany : Microsoft CorporationFile Version : 6.3.9600.17736 (winblue_r9.150322-1500)Processor : x64Crash Address : ntoskrnl.exe+150ca0Stack Address 1 :Stack Address 2 :Stack Address 3 :Computer Name :Full Path : C:\WINDOWS\Minidump\072715-33859-01.dmpProcessors Count : 4Major Version : 15Minor Version : 9600Dump File Size : 281,520Dump File Time : 27/07/2015 05:12:34 pm====================================================================================================Dump File : 072715-48062-01.dmpCrash Time : 27/07/2015 05:00:25 pmBug Check String : BAD_POOL_CALLERBug Check Code : 0x000000c2Parameter 1 : 00000000`00000007Parameter 2 : 00000000`00001200Parameter 3 : 00000000`00000000Parameter 4 : ffffe000`4bc1b4c8Caused By Driver : ntoskrnl.exeCaused By Address : ntoskrnl.exe+150ca0File Description : NT Kernel & SystemProduct Name : Microsoft® Windows® Operating SystemCompany : Microsoft CorporationFile Version : 6.3.9600.17736 (winblue_r9.150322-1500)Processor : x64Crash Address : ntoskrnl.exe+150ca0Stack Address 1 :Stack Address 2 :Stack Address 3 :Computer Name :Full Path : C:\WINDOWS\Minidump\072715-48062-01.dmpProcessors Count : 4Major Version : 15Minor Version : 9600Dump File Size : 281,520Dump File Time : 27/07/2015 05:01:58 pm==================================================Frustratingly, since there are so many variables involved (unscientific method!), it seems like I'm playing a Jenga game with trying to make this work, since if I remove, or change something, it works for a little while, and then crashes in a creative, new way. (And I don't want to reinstall everything, since I don't have a disk big enough to back everything up). :(I've uploaded a copy of the Nurago Web Meter to https://dl.dropboxusercontent.com/u/670345/nurago%20web%20meter.exe, and I seem to also have an older installer for it in my "Downloads" directory, which may exercise the LSP architecture of WinSock differently.The SYSTEM_SERVICE_EXCEPTION error is interesting, as it is one of the few that reveals a problem in WinSock/NDIS...I would try it in a virtual machine - but it wouldn't get us any closer to diagnosing why it fails to work, with my not-so-unique configuration.Tyson.2015-07-28 7:27 GMT+01:00 Yang Luo <hsluoyb@xxxxxxxxx>:___________________________________________________________________________On Mon, Jul 27, 2015 at 10:42 PM, Tyson Key <tyson.key@xxxxxxxxx> wrote:After rebooting from uninstalling MS NetMon, I restarted Wireshark, and got the usual "NPF service not running; no interfaces available" note. This persists, even if I try "NPFInstall -r", and Wireshark still claims that no interfaces are available."NPFInstall -r" isn't used in Npcap. "NPF service not running; no interfaces available" is a common problem for Npcap previous versions. And I think it should disappear if you have uninstalled previous versions totally.Eventually, after uninstalling NPCap, removing all of the loopback interfaces, and running CCleaner to remove any residual registry data, and then rebooting yet again, I could start Wireshark, and list the installed interfaces - but unsurprisingly, a few moments later, I received another BSoD.If it helps, my Wireshark version is:Version 1.99.8-492-g3f0f49d (v1.99.8rc0-492-g3f0f49d from master)Copyright 1998-2015 Gerald Combs <gerald@xxxxxxxxxxxxx> and contributors.License GPLv2+: GNU GPL version 2 or later <http://www.gnu.org/licenses/old-licenses/gpl-2.0.html>This is free software; see the source for copying conditions. There is NOwarranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.Compiled (64-bit) with GTK+ 2.24.23, with Cairo 1.12.16, with Pango 1.36.8, withWinPcap (unknown), with libz 1.2.8, with GLib 2.42.0, with SMI 0.4.8, withc-ares 1.9.1, with Lua 5.2, with GnuTLS 3.2.15, with Gcrypt 1.6.2, with MITKerberos, with GeoIP, with PortAudio V19-devel (built Jul 22 2015), withAirPcap.Running on 64-bit Windows 8.1, build 9600, with locale English_UnitedKingdom.1252, with Npcap version 0.01 (packet.dll version 0.03), based onWinPcap version 4.1.3 (packet.dll version 4.1.0.3001), based on libpcap version1.0 branch 1_0_rel0b (20091008), with GnuTLS 3.2.15, with Gcrypt 1.6.2, withoutAirPcap.AMD A6-5200 APU with Radeon(TM) HD Graphics (with SSE4.2), with 5577MB ofphysical memory.Built using Microsoft Visual C++ 12.0 build 31101Wireshark is Open Source Software released under the GNU General Public License.Check the man page and http://www.wireshark.org for more information.I used Wireshark latest stable version: Version 1.12.6 (v1.12.6-0-gee1fce6 from master-1.12). But I don't think it makes a difference by using stable version or development version, as its WinPcap related low-level code rarely changed between these two versions.Other than NetMon (which I've removed), the only other things that I think could be causing a conflict are either the VMware host-only networking filters; the networking components included with whatever Bluetooth stack Lenovo shipped; the massive pile of hacks installed by the Gacela component of "Nurago Web Meter", or my Atheros WLAN drivers (which caused Acrylic Wi-Fi's NDIS filters to crash, when I briefly had that installed, a while ago).What version VMware are you using? Workstation or just Player? I used VMware Workstation 11.1.2 build-2780323 on my host, but I didn't install it on my test VM yet.Cheers,Yang
Sent via: Wireshark-dev mailing list <wireshark-dev@xxxxxxxxxxxxx>
Archives: https://www.wireshark.org/lists/wireshark-dev
Unsubscribe: https://wireshark.org/mailman/options/wireshark-dev
mailto:wireshark-dev-request@xxxxxxxxxxxxx?subject=unsubscribe--http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844Fight Internet Censorship! http://www.eff.org--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844
___________________________________________________________________________
Sent via: Wireshark-dev mailing list <wireshark-dev@xxxxxxxxxxxxx>
Archives: https://www.wireshark.org/lists/wireshark-dev
Unsubscribe: https://wireshark.org/mailman/options/wireshark-dev
mailto:wireshark-dev-request@xxxxxxxxxxxxx?subject=unsubscribe
___________________________________________________________________________
Sent via: Wireshark-dev mailing list <wireshark-dev@xxxxxxxxxxxxx>
Archives: https://www.wireshark.org/lists/wireshark-dev
Unsubscribe: https://wireshark.org/mailman/options/wireshark-dev
mailto:wireshark-dev-request@xxxxxxxxxxxxx?subject=unsubscribe--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844
___________________________________________________________________________
Sent via: Wireshark-dev mailing list <wireshark-dev@xxxxxxxxxxxxx>
Archives: https://www.wireshark.org/lists/wireshark-dev
Unsubscribe: https://wireshark.org/mailman/options/wireshark-dev
mailto:wireshark-dev-request@xxxxxxxxxxxxx?subject=unsubscribe
___________________________________________________________________________
Sent via: Wireshark-dev mailing list <wireshark-dev@xxxxxxxxxxxxx>
Archives: https://www.wireshark.org/lists/wireshark-dev
Unsubscribe: https://wireshark.org/mailman/options/wireshark-dev
mailto:wireshark-dev-request@xxxxxxxxxxxxx?subject=unsubscribe--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844--Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844
Fight Internet Censorship! http://www.eff.org
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844
http://vmlemon.wordpress.com | Twitter/FriendFeed/Skype: vmlemon | 00447934365844
- Follow-Ups:
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- References:
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Yang Luo
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- From: Tyson Key
- Re: [Wireshark-dev] Npcap 0.03 call for test
- Prev by Date: Re: [Wireshark-dev] Npcap 0.03 call for test
- Next by Date: Re: [Wireshark-dev] Npcap 0.03 call for test
- Previous by thread: Re: [Wireshark-dev] Npcap 0.03 call for test
- Next by thread: Re: [Wireshark-dev] Npcap 0.03 call for test
- Index(es):