Hi All,
We see an issue when decoding packets sniffed from a Cisco Sniffer AP using PEEKREMOTE.
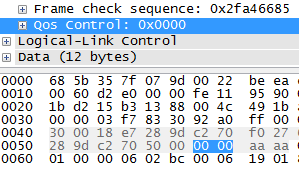
The header for “IEEE 802.11 QoS Data” under “AiroPeek/OmniPeek encapsulated IEEE 802.11” is found to be of 28 bytes in length. Whereas the same ““IEEE 802.11 QoS Data” under default decoding is 26 bytes for “LLC” packets. This leads to
the fist 2 bytes of LLC to go wrongly under “IEEE 802.11 QoS Data”, which in turn leads to LLC DSAP as unknown and Wireshark is not able to identify EAP/EAPOL packets.
The following are the screen shots from the capture.

The two bytes highlighted are not a part “QOS Control” which is the last field in “IEEE 802.11 QoS Data”.
The same packets are decoded properly with 26 bytes header by “WildPackets Omnipeek” as shown below.

For packets captured over the air with sniffer laptops (default decoding and not PEEKREMOTE), the “IEEE 802.11 QoS Data” is correctly decoded with 26 bytes header as EAP/EAPOL is identified.

Please provide your thoughts on how we can resolve this issue as we are seeing this in multiple sniffer setups using Wireshark.
Thanks,
Vignesh



